White Screen on WordPress Site – link-template.php.suspected
We’ve been having a recurring problem on a WordPress website despite everything being up-to-date and clean according to Sucuri. The site seemed to go down every day, and present anyone visiting it with a blank white screen;
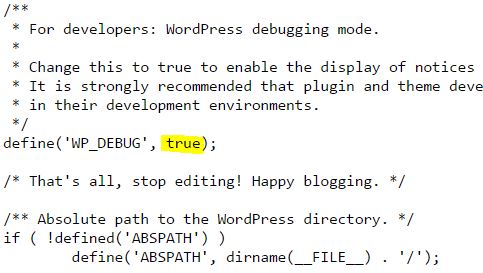
By default WordPress hides the error messages, so we have to change this to “True” in wp-config.php for error messages to start showing;
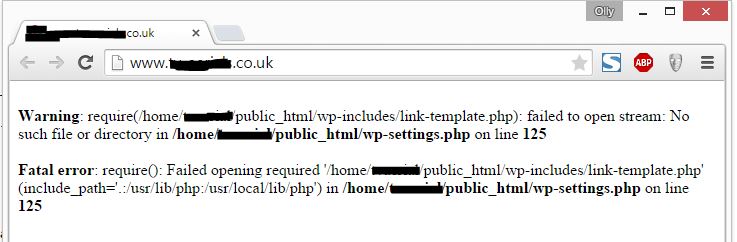
Once we save wp-config.php and then try and visit the website again we now get this;
This error is telling me that the file link-template.php seems to be missing? How bizarre. I went into cpanel file manager and browsed to wp-includes/ and this is what I found;
Ok, so thats weird. I renamed it back to link-template.php and the site pinged back into life.
So why/how did this file get renamed?
Well in all honesty i’m still working that out, but after doing much searching and reaching out on Twitter I came to the conclusion that it is due to the fact this site – at some point in its life – has been the victim of a hack and the files were not fully cleaned afterwards.
My first port of call is always a deep file scan by our security partner, they found a number of files that were in fact infected and we got them all cleaned up.
However, a few days later;
Again!
So I reached out to our security partner once again, they told me;
“Your site is clean already and was not reinfected. The warning was caused by a temporary hosting error (that generated a 500/internal server error).”
Hmm, well why did the link-template.php file get renamed if the site is now clean?
After a few more rounds of coming into work to find it down again, I decided to try some more fixes that were referenced on this WordPress forum post. The SSH commands I used were;
egrep -Rl ‘function.*for.*strlen.*isset’ /home/username/public_html/
and
egrep -Rl ‘\$GLOBALS.*\\x’ /home/username/public_html
The username part needs changing to the name of the Linux user for that particular hosting account. These commands search through file contents looking for certain references that you generally only find in Hacked files, and sure enough these commands found about 10 files that our deep security scanning missed.
I cleared those files up and am continuing to monitor the website, but so far so good!
If you have got into work to find a white screen on your wordpress website, or you keep getting hacked and cant seem to stop it then give our internet security team a call on 441623 650333 or contact us using the details dotted about our website.